Mastering Micro-Segmentation: North-South vs. East-West Strategies

This article is part of our series on Zero Trust. For more information on Zero Trust, check out Zero Trust, Explained.
North-South and East-West
Micro-segmentation is one of the core functions of a next-generation Zero Trust cybersecurity solution, as it allows the security functions to be inserted in front of a workload to distrust the network. But not all micro-segmentation is created equally. It turns out that the implementation of the micro-segmentation zero trust function has a major impact on how thoroughly it can implement a Zero Trust Architecture. To understand why, let's examine the two major directions traffic can flow: north-south, and east-west.
What Is North-South Traffic?
A "north-south" flow of traffic refers to traffic that goes through one or more aggregation points to get to the destination. In the example diagram below, traffic from host A to the cloud host B is aggregated together with all other traffic from the same subnet by the leaf router, and forwarded toward the enterprise edge, where it is then sent on to the cloud.
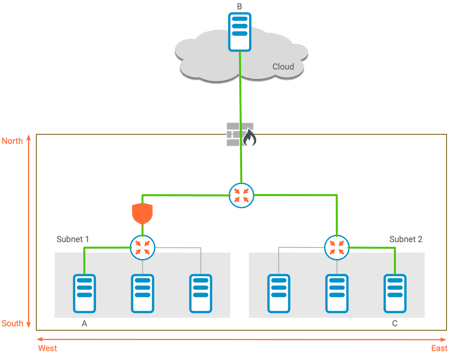
North-South Traffic Can be Filtered at an Aggregation Point
While it may be slightly less obvious, traffic from host A to host C is also considered north-south; it travels northward toward the spine, and then southward again toward host C's router.
Because north-south traffic is aggregated, there is naturally a point in the network where a filtering function (the shield in the diagram) could be inserted to perform a security function. This "north-south" micro-segmentation can therefore secure traffic between host A and hosts B or C.
What Is East-West Traffic?
In contrast to north-south traffic, the traffic between host A and host D shown below is in the "east-west" direction. The two hosts are in the same subnet, and have a point-to-point connection between them.
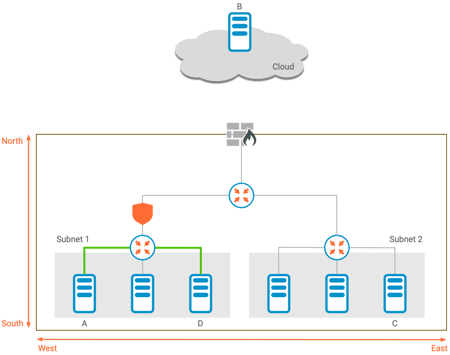
East-West Traffic Does Not Pass Through the Aggregation Point
As east-west traffic is not aggregated, the security filter at the aggregation point that worked for the north-south case above is ineffective.
It turns out that the east-west case is fairly common; most network traffic travels in an east-west direction.
Micro-Segmentation Zero Trust vs Software-Defined Perimeters
Proper application of Zero Trust principles requires that traffic from other hosts on the network should not be trusted. A solution that handles the north-south direction, but doesn't protect east-west, implicitly trusts all other machines on the same subnet.
For a NIST 800-207 Zero Trust Architecture, it's important to create an implicit trust zone around the resource being protected - east-west traffic must also go through the Policy Enforcement Point. This can be done with a tool called a Software-Defined Perimeter, which is a close cousin of micro-segmentation. A Software-Defined Perimeter protects resources both in the north-south and east-west directions, creating the smallest possible implicit trust zone around a resource.
SDPs and micro-segmentation share a lot in common, at the technical level. However, micro-segmentation solutions are typically targeted for datacenter-scale visibility. These solutions often aren't optimized for Zero Trust, and may have business models that aren't cost effective for a Zero Trust implementation.
For example, both micro-segmentation zero trust and SDPs support agent-based deployment models that protect applications at the OS level. Technically, both are capable of filtering north-south and east-west traffic, and can work well in any datacenter, cloud, or containerized environment. However, the micro-segmentation tool may expect that all servers use the agent; a typical SDP can be deployed easily and cost-effectively on a single server, if needed.
Both also support agentless deployment models, as may be required for OT environments. For a true agentless deployment, Zentera recommends an SDP gatekeeper approach, as implemented by the Zentera Micro-Segmentation Gatekeeper (MSG). This model enables each workload to be protected with a Zero Trust DMZ, without having to touch the workload itself.


