What is a Zero Trust DMZ for OT?

This article is part of our series on Zero Trust. For more information on Zero Trust, check out Zero Trust, Explained.
What is a network DMZ?
A demilitarized zone, or "DMZ", is one of the workhorses of network security architecture. A DMZ refers to a small network that is placed between a corporate network and the Internet. The DMZ exposes a small number of services to the Internet, subjecting access from outside the company to security scanning and filtering based on corporate policies. On the outbound path, the DMZ applies policies on traffic to the Internet.
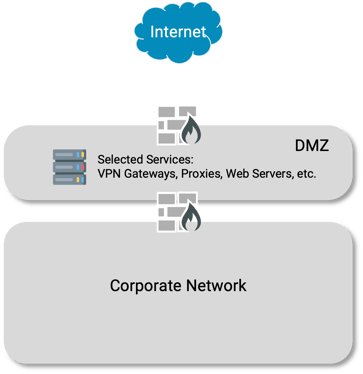 A traditional DMZ filters both inbound and outbound traffic, applying policies to traffic between two networks.
A traditional DMZ filters both inbound and outbound traffic, applying policies to traffic between two networks.
Deployed this way, the DMZ effectively segments the corporate network from the Internet.
What's a Zero Trust DMZ?
A Zero Trust DMZ is a DMZ which is deployed to enforce Zero Trust policies, supporting authentication and authorization of the traffic that flows through it. A Zero Trust DMZ can be implemented virtually by inserting a Micro-Segmentation Gatekeeper (MSG) in front of a resource or subnet to be protected, as shown below.
 The MSG deploys inline with devices or subnets to create a Zero Trust DMZ, segmenting them from the rest of the network.
The MSG deploys inline with devices or subnets to create a Zero Trust DMZ, segmenting them from the rest of the network.
This can be a very effective method for segmenting an OT network without disrupting brownfield infrastructure or affecting any of the running applications. As a result, the Zero Trust DMZ is a powerful new architecture concept for IT-OT convergence.
With the MSG, the Zero Trust DMZ can also terminate ZTNA accesses from within the company, or from remote users. This can be used to give partners or vendors direct access to specific machines within the OT environment, without exposing the entire environment.
How is this OT Zero Trust DMZ different from an OT Firewall?
It's true that you can use a firewall to segment an OT network, but a few issues make it challenging to use them to protect devices or subnets.
First, OT firewalls will provide a lower level of protection. That's because they can't implement Zero Trust. That's because they operate on information available in packets - Layer 2, Layer 3, and so on. An OT firewall could implement UTM functions, like intrusion detection, or simple filtering, but the information needed to perform authentication and authorization needed to apply a Zero Trust policy simply isn't available at that level.
Second, firewalls are typically designed with one logical uplink and one or more logical downlink ports. It may not be cost-effective or easy to manage a deployment with individual firewalls in front of each resource. In contrast, Zentera's MSG supports up to 32 port-pairs, making it easy to protect up to 32 devices or subnets, with centralized management for all MSGs provided by the zCenter orchestrator.




