Complete visibility into application behavior, with exporting to popular log monitors such as Splunk and ELK, as well as the corporate SIEM.





CoIP Platform provides a complete solution for rapidly onboarding users and endpoints of all kinds into a Zero Trust Security framework.


CoIP Platform authenticates users, endpoints, and applications, using corporate identity providers, certificates, and other device/app fingerprints.
When a user or application requests access, CoIP Platform checks policy, sets up a CoIP AppLink tunnel for authorized connections if required, and inserts required security functions inline, such as firewall and threat detection/prevention.
CoIP Platform supports nearly any cloud environment, bare metal, or IoT device with agent-based, agentless, and gatekeeper deployment options, and deploys in existing environments without requiring network and security infrastructure changes.
CoIP Platform provides administrators with complete visibility into user, endpoint, and application end-to-end behavior. It provides powerful control over the cyber kill chain for response and remediation.
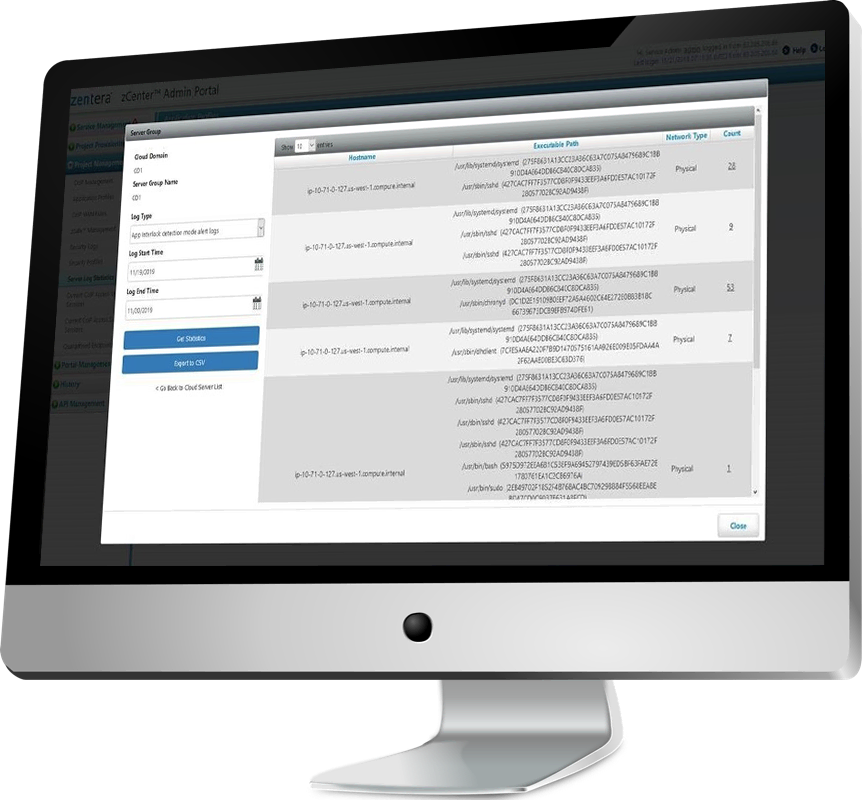
Complete visibility into application behavior, with exporting to popular log monitors such as Splunk and ELK, as well as the corporate SIEM.

Application communications are defined by whitelist policies, creating security by default. Policies are end-to-end, creating a single, global policy database that defines who can access what resource.
The Application Profile concept enables a set of policies to be defined as a template and used again and again.
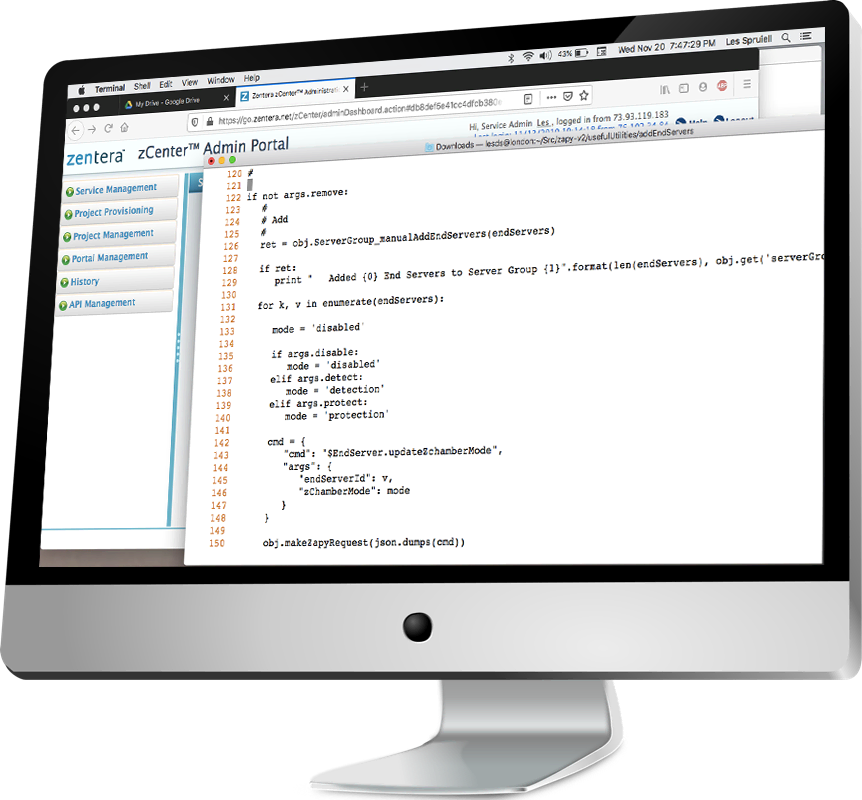
CoIP Platform's rich APIs enable infrastructure-as-code deployment for simple, repeatable deployment of applications in complex hybrid infrastructure.
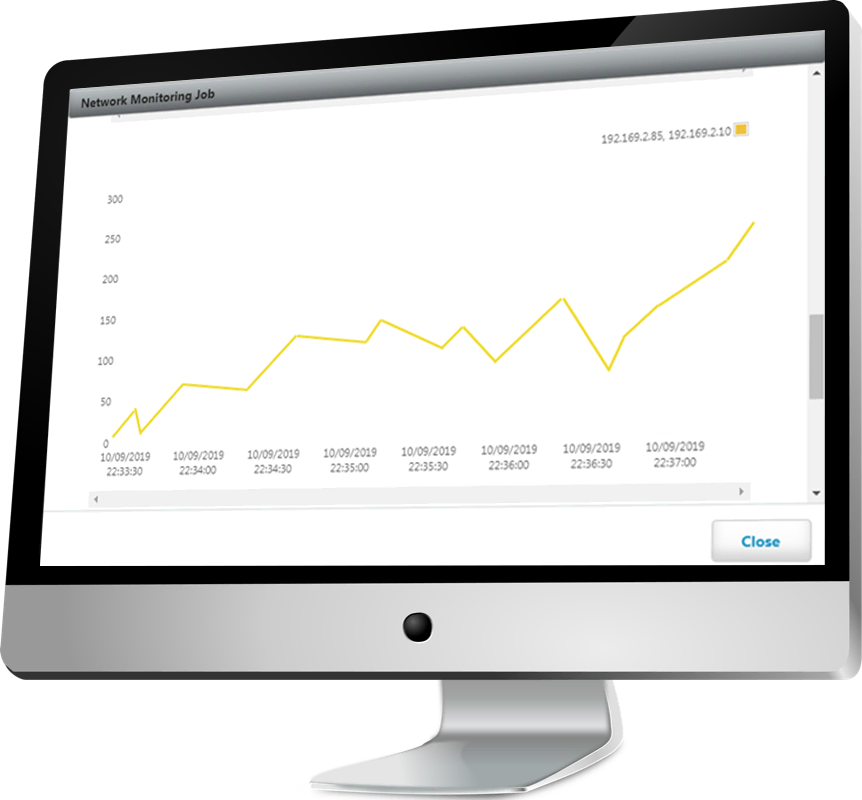
CoIP Platform enables administrators to track throughput and performance with flow monitoring.

Complete visibility into application behavior, with exporting to popular log monitors such as Splunk and ELK, as well as the corporate SIEM.

Application communications are defined by whitelist policies, creating security by default. Policies are end-to-end, creating a single, global policy database that defines who can access what resource.
The Application Profile concept enables a set of policies to be defined as a template and used again and again.

CoIP Platform's rich APIs enable infrastructure-as-code deployment for simple, repeatable deployment of applications in complex hybrid infrastructure.

CoIP Platform enables administrators to track throughput and performance with flow monitoring.

Complete visibility into application behavior, with exporting to popular log monitors such as Splunk and ELK, as well as the corporate SIEM.
Learn about the Architecture and Components
Review our video and whitepaper resources
Review our additional design support resources and tools
Get CoIP Platform:
Contact us for questions and support
CoIP Platform is simple to deploy. Completely built out of computing elements and with physical and virtual appliance options, CoIP Platform can be spun up in your data center or in the cloud.
CoIP Platform is non-intrusive and can be deployed to a running application server without requiring a restart. Once deployed, administrators can build and test policies in the running environment before turning on security protections.
CoIP Platform offers a full suite of diagnostic and monitoring APIs that integrate into your operational flow, and rich data can be exported to a SIEM, such as Splunk or ELK, for further processing.
In addition to our library of resources and training videos, Zentera's experienced engineers and architects are available to provide training, architecture guidance, and to advise operational best practices for your projects.
“CoIP Access Platform’s best-in-class micro-segmentation keeps our customers secure, and we and our customers have saved a significant amount of time in configuration and deployment.”
“With the CoIP Access Platform, we are able to protect our IP and segment our resources across worldwide infrastructures almost instantly.”
“With CoIP, we are able to onboard our design partners and EDA vendors in a matter of days instead of weeks or months, which provides us with a great advantage in our product design and development agility. That is critical in our fast-moving industry.”
“With the CoIP solution, you are literally connecting the one person that needs access to the one resource they need access to and nothing else.”
“CoIP Access Platform’s best-in-class micro-segmentation keeps our customers secure, and we and our customers have saved a significant amount of time in configuration and deployment.”
“With the CoIP Access Platform, we are able to protect our IP and segment our resources across worldwide infrastructures almost instantly.”
“With CoIP, we are able to onboard our design partners and EDA vendors in a matter of days instead of weeks or months, which provides us with a great advantage in our product design and development agility. That is critical in our fast-moving industry.”
“With the CoIP solution, you are literally connecting the one person that needs access to the one resource they need access to and nothing else.”
“CoIP Access Platform’s best-in-class micro-segmentation keeps our customers secure, and we and our customers have saved a significant amount of time in configuration and deployment.”
“With the CoIP Access Platform, we are able to protect our IP and segment our resources across worldwide infrastructures almost instantly.”
Sign up for our newsletter and to be notified of product, solution, and company news.
© 2025 Zentera Systems, Inc. Terms of Service Privacy Policy Open Source