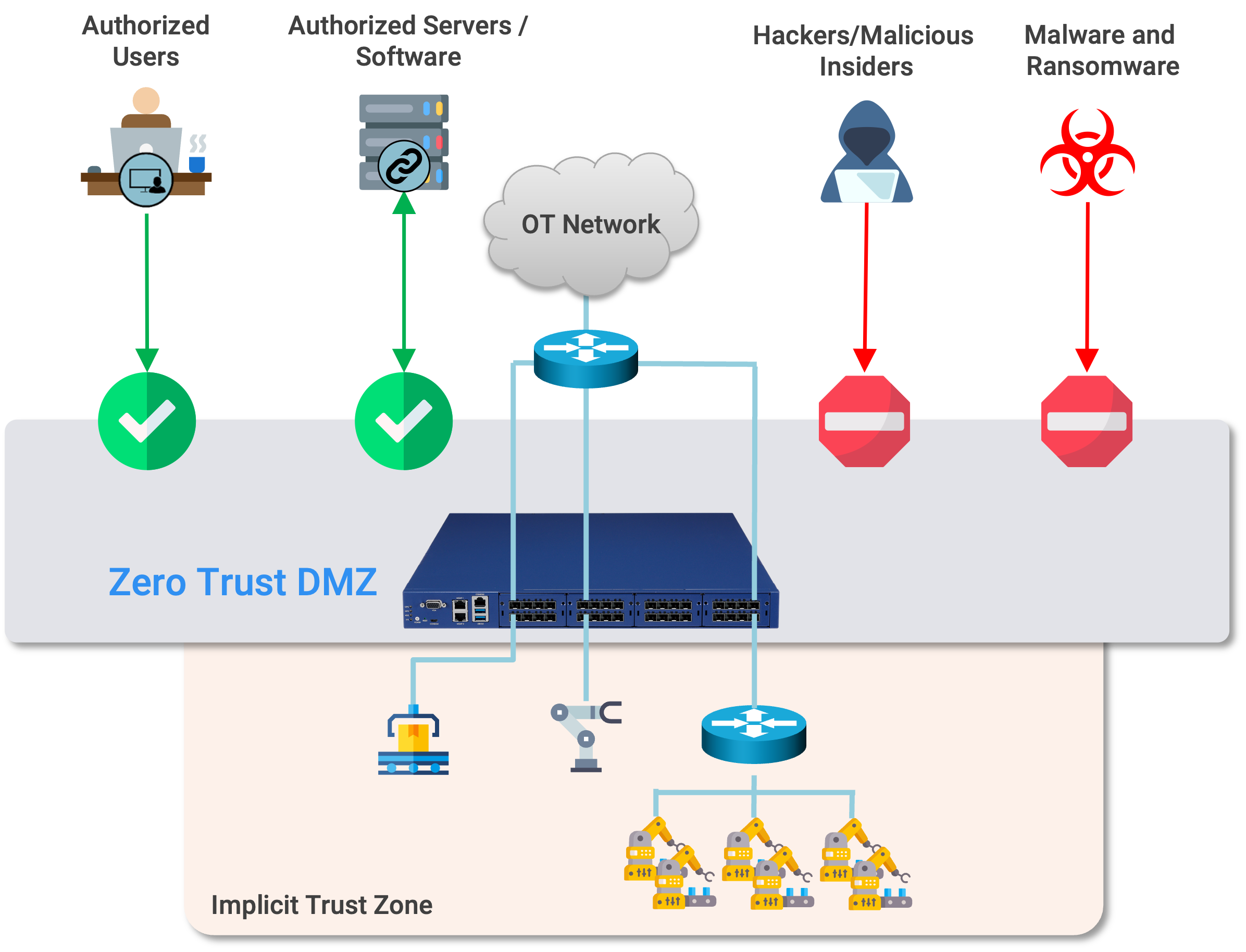
When major U.S. utilities began discovering unauthorized access in their operational systems in early 2023, initial investigations suggested routine compliance issues. The reality, however, was far more concerning: a sophisticated state-sponsored ...
Read